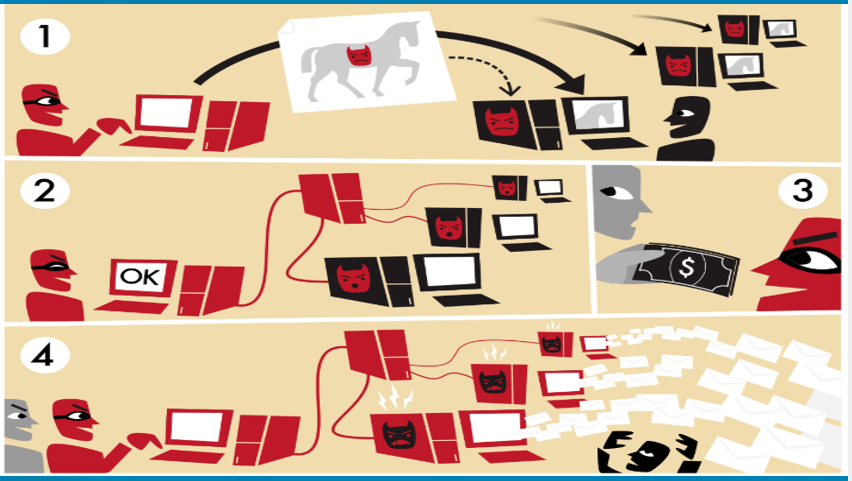
WASHINGTON / THE HAGUE — May 26, 2025 — In a major international cybercrime takedown, law enforcement agencies from the United States, Europe, and other global partners have disrupted the infamous DanaBot botnet, dismantling its vast infrastructure and unsealing indictments against 16 individuals allegedly involved in its operations.
The coordinated action, part of the broader Operation Endgame, targeted malware-as-a-service ecosystems that have long plagued digital infrastructure worldwide. Authorities dismantled over 300 servers and 650 domains linked to DanaBot and other reemergent malware strains, such as Lumma Stealer, SmokeLoader, TrickBot, and Bumblebee.
According to the U.S. Department of Justice, DanaBot infected more than 300,000 devices globally and facilitated a range of cyberattacks — from banking fraud to ransomware — causing financial losses estimated at over $50 million. The malware had operated since 2018 and was initially deployed in Ukraine, Poland, Austria, Italy, Germany, and Australia, before spreading to North America.
Authorities also seized $24 million in cryptocurrency assets, including $4 million directly linked to DanaBot operations.
Key Suspects Identified
Two central figures in the botnet’s development and administration were named in unsealed court documents: Aleksandr Stepanov, 39 (aka “JimmBee”), and Artem Kalinkin, 34 (aka “Onix”), both residents of Novosibirsk, Russia. Kalinkin, reportedly an IT engineer for Russian energy conglomerate Gazprom, faces up to 72 years in prison if extradited and convicted. Stepanov faces a maximum five-year sentence.
Despite the indictments, both suspects remain at large. Investigators revealed that several perpetrators were identified after inadvertently infecting their own systems with DanaBot, exposing critical operational details.
Strategic Threat and Espionage Allegations
Originally a banking trojan, DanaBot evolved into a highly adaptable delivery platform for various malware strains. Cybersecurity researchers, including those at Proofpoint and CrowdStrike, noted its resurgence in mid-2024, utilizing malvertising and SEO poisoning after declining in email-based campaigns.
CrowdStrike, which tracks the threat actor group behind DanaBot as “Scully Spider,” emphasized the group’s connections to broader geopolitical objectives. Some DanaBot subnetworks were reportedly used to assist Russian military operations and conduct cyber-espionage targeting diplomats, law enforcement officials, and military personnel across North America and Europe.
Multinational Collaboration
The success of the operation was made possible through joint efforts by Europol, the FBI, and national cybersecurity agencies, alongside private sector partners such as Lumen Technologies (Black Lotus Labs), Team Cymru, and ESET. These partners provided intelligence and infrastructure mapping vital to the takedown.
“This takedown marks a significant disruption of a dangerous malware-as-a-service ecosystem,” said an ESET spokesperson. “It remains to be seen whether DanaBot can recover, but the law enforcement response has undoubtedly shaken its foundation.”
Broader Implications
DanaBot’s dismantling highlights both the persistence of transnational cybercriminal networks and the growing effectiveness of collaborative countermeasures. Authorities say they will continue pursuing remaining suspects and urge governments to remain vigilant as cyber threats evolve.
For more information, visit justice.gov or europol.europa.eu.
Botnets Functioning Infographic Picture by Tom-b